What is BWall ransomware? And how does it carry out its attack?
BWall ransomware is one of the latest crypto-viruses discovered at the end of September 2019. This new crypto-virus adds a “.bwall” extension to every file it corrupts. Just like other ransomware threats, BWall ransomware can leave your files useless and inaccessible once it carries out its attack. It starts its attack by dropping its payload file in the system which will be followed by its other malicious components.
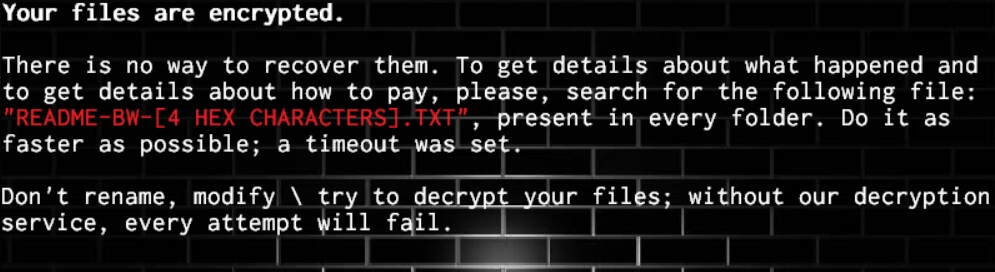
After it places its malicious components in system folders, BWall ransomware will modify the Windows Registry so that it can resume its attack every time a victim turns on the infected computer. It also launches and represses system processes making it a persistent threat. Aside from that, it also employs data gathering module and stealth protection module. The first module is used to obtain information from the computer that will be used for the next module. The second module is used to prevent any security and antivirus programs from interrupting the attack. Once the system modifications are completely implemented, BWall will start encrypting its targeted files using a combination of AES and RSA ciphers. Once the encryption is completed, it attaches the “.bwall” suffix to every affected file and opens its ransom note named “HOW_DECRYPT_FILES.txt” that states:
“Your files are encrypted!
Your files (documents, pictures, audio files, source codes) were encrypted with
combination of AES-256 and RSA-4096 cryptagr aphic algorithms. your files will
not be deccryptable, without our specia decryption service; futhermore, there is
an condition that will leave your files encrypted forever if it’s not met:
there is a deadline to pay for your data! If that is exceeded, we will not let you
decrypt your data (we will not offer any kind of service). You have exactly two weeks
to decrypt your data! No recovery tool will help you, such as Recuva, and no Microsoft
feature will help (shadow Copies>. Files with “.bw” extension are encrypted. verify.
The current date time was inserted into the ID, and we can guess every patching attempt.
End of the deadline: HU-HU-HAI
To pay for your files, follow these steps :
1) Set-up a BitCoin account. we cannot help you in that, but you can search on
Google or similar for “bitcoin get started” or “bitcoin help”. You can skip
this step, if you have already one; we also accept Monero as currency, and we’ll
give a discount if an anonymous currency like that is used (20%). Do the same
research to set-up a Monero account if you don’t have one, as well.
2) send the following amount of money (0,018 BTC) to the following Bitcoin address,
and keep the TXID (payment \ transaction ID) for later:
1P7VBy5YLBRXxNiTjJBCQUEzyr yZEcfdQwGD
Monero address, for “getting a discount”:
44NMuci8TSUI4TBafyJpQDAHjTEStCObXwAVmB31mJiaCZFGxotyfZ5LW83VQYdHKM5DG313aFsw7fjnc8ga9JBk6bwAuHa
3) after, send this file and the TxID of before to the following e-mail address, with
the subject “Decryption” and with a e-mail address that can receive e-mails at every
moment; don’t use temporary services, we will reply after six hours at least:
[email protected]
4) wait, you will get an e-mail with even more istructions, and, the decryptor.
Don’t rename, modify, or try to decrypt your files without our special service.
Don’t modify this text file! Don’t make decryption impossible even for us.
ID: KILL-ID
Don’t modify the ID! Remember, any bad words to our side will make your address banned!
Also, please, don’t try to patch or decompile the decryptor once you get it, it doesn’t
contain the private key of the encryption algorithm.”
Paying the ransom should not be part of your recovery solution as there really is no guarantee that the crooks behind BWall ransomware will do their end of the bargain once they receive the ransom payment. Usually victims of ransomware threats are ignored by crooks that had successfully deceived them into paying the ransom.
How does BWall ransomware proliferate?
It isn’t clear yet how exactly BWall ransomware proliferate but it could be using one of the most common distribution method of ransomware threats like malicious spam email campaigns that might contain a .docx file attachment with macro scripts. This macro-enable document is the one who will connect the system into the Command and Control server of BWall ransomware. Because of this, you need to be careful when opening any kinds of email from your inbox as it might contain a malicious file that could be used to install threats like BWall ransomware into your computer.
Using the removal guide provided below, obliterate BWall ransomware from your computer and all of its malicious components.
Step 1: Close the ransom note of BWall ransomware and end its malicious processes via Task Manager. To open it, tap Ctrl + Shift + Esc keys on your keyboard.
Step 2: Under the Task Manager, go to the Processes tab and look for any suspicious-looking process that takes up most of your CPU’s resources and is most likely related to BWall ransomware.

Step 3: After that, close the Task Manager.
Step 4: Tap Win + R, type in appwiz.cpl and click OK or tap Enter to open Programs and Features under Control Panel.
Step 5: Under the list of installed programs, look for BWall ransomware or anything similar and then uninstall it.

Step 6: Next, close Control Panel and tap Win + E keys to launch File Explorer.
Step 7: Navigate to the following locations below and look for BWall ransomware’s malicious components such as HOW_DECRYPT_FILES.txt, [random].exe and other suspicious files, then delete all of them.
- %TEMP%
- %WINDIR%\System32\Tasks
- %APPDATA%\Microsoft\Windows\Templates\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 8: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name], this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 9: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 10: Navigate to the following path:
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 11: Delete the registry keys and sub-keys created by BWall ransomware.
Step 12: Close the Registry Editor and empty the Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if BWall ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

Using the advanced removal guidelines provided below, complete the removal process of BWall ransomware.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot it.
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.

- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.

- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.

- After the scan is completed click the “Fix, Clean & Optimize Now” button.